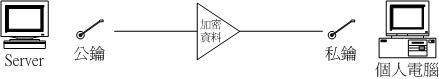
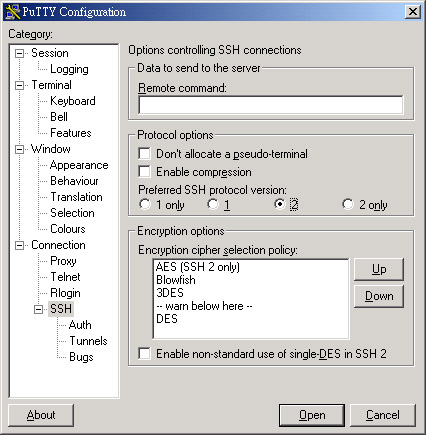
# 1. SSH
Server ]wA]tϥΪ port աAHΨϥΪKXt觋
Port 22@@@@@@@@@@#
SSH w]ϥ 22 o portAz]iHϥΦh port I
@@@@@@@@@@@@@
# Yƨϥ port oӳ]wاYiI
Protocol 2,1@@@@@@@
#
ܪ SSH wAiHO 1 ]iHO 2 A
@@@@@@@@@@@@@
# pGnPɤ䴩̡ANnϥ 2,1 oӤjFI
#ListenAddress
0.0.0.0@@ # ťDdI|ӨҤlӻApGz
IPA
@@@@@@@@@@@@@
# OO 192.168.0.100 192.168.2.20 AuQn
@@@@@@@@@@@@@
# } 192.168.0.100 ɡANiHgpPU˦G
ListenAddress
192.168.0.100 #
uťӦ 192.168.0.100 o IP SSHsuC
@@@@@@@@@@@@@@@@@@
# pGϥγ]wܡAhw]Ҧ SSH
PidFile /var/run/sshd.pid@@@@@@#
iHm SSHD o PID ɮסICw]
LoginGraceTime
600@@@@ # ϥΪ̳sW SSH server A|X{JKXeA
@@@@@@@@@@@@@
# bӵeAbh[ɶS\sW SSH server A
@@@@@@@@@@@@@
# N_uIɶI
Compression
yes@@@@@@# O_iHϥYOHMiHoI
@
# 2. D
Private Key mɮסAw]ϥΤUɮקYiI
HostKey /etc/ssh/ssh_host_key@@@@#
SSH version 1 ϥΪp_
HostKey /etc/ssh/ssh_host_rsa_key@@#
SSH version 2 ϥΪ RSA p_
HostKey /etc/ssh/ssh_host_dsa_key@@#
SSH version 2 ϥΪ DSA p_
# 2.1 version
1 @dz]wI
KeyRegenerationInterval
3600@ @@@# ѫesuiHDA
version 1 |ϥ
@@@@@@@@@@@@@@@@@@
# server Public Key ApGo Public
@@@@@@@@@@@@@@@@@@
# Key QܡAZJHҥHݭnCj@qɶ
@@@@@@@@@@@@@@@@@@
# ӭsإߤ@Io̪ɶI
ServerKeyBits
768 @@@@@@@@@ # SIoӴNO Server
key סI
# 3. nɪTƩmP
daemon W١I
SyslogFacility
AUTH@@@@@@@@@# Hϥ SSH nJtΪɭԡASSH|O
@@@@@@@@@@@@@@@@@@
# TAoӸTnOb daemon name UH
@@@@@@@@@@@@@@@@@@
# w]OH AUTH ӳ]wAYO /var/log/secure
@@@@@@@@@@@@@@@@@@
# ̭IHѰOFI^ Linux ¦h½@U
@@@@@@@@@@@@@@@@@@
# LiΪ daemon name GDAEMON,USER,AUTH,
@@@@@@@@@@@@@@@@@@
# LOCAL0,LOCAL1,LOCAL2,LOCAL3,LOCAL4,LOCAL5,
LogLevel INFO@@@@@@@@@@@@#
nOšIKKITI
@@@@@@@@@@@@@@@@@@
# P˪AѰOFN^hѦҡI
# 4. w]wءInI
# 4.1 nJ]w
PermitRootLogin
no@@ @@# O_\ root nJIw]O\AOij]w
noI
UserLogin no@@@@@@@
# b SSH UӴN login oӵ{nJI
StrictModes
yes@@@@@@# ϥΪ̪ host key ܤAServer
NsuA
@@@@@@@@@@@@@
# iH׳차{I
#RSAAuthentication
yes@@ # O_ϥίª RSA {ҡIHȰw
version 1 I
PubkeyAuthentication
yes@ # O_\ Public Key HM\աIu
version 2
AuthorizedKeysFile
.ssh/authorized_keys
@@@@@@@@@@@@@
# WoӦb]wYnϥΤݭnKXnJbɡA
@@@@@@@@@@@@@
# bsɮשҦbɦWI
# 4.2 {ҳ
RhostsAuthentication
no@@# tΤϥ .rhosts A]Ȩϥ
.rhosts
@@@@@@@@@@@@@
# wFAҥHo̤@wn]w no I
IgnoreRhosts
yes@@@@@ # O_ϥ ~/.ssh/.rhosts
Ӱ{ҡIMOI
RhostsRSAAuthentication
no # oӿﶵOM version 1 ΪAϥ
rhosts ɮצb
@@@@@@@@@@@@@
# /etc/hosts.equivtX RSA t觋Ӷi{ҡInϥ
HostbasedAuthentication
no # oӶػPWALO version
2 ϥΪI
IgnoreUserKnownHosts
no@@# O_aؿ ~/.ssh/known_hosts
oɮשҰO
@@@@@@@@@@@@@
# DeHMnAҥHo̴NO no աI
PasswordAuthentication
yes # KXҷMOݭnIҥHo̼g yes
oI
PermitEmptyPasswords
no@@# YW@pG]w yes ܡAo@N̦n]w
@@@@@@@@@@@@@
# no AoӶئbO_\HŪKXnJIM\I
ChallengeResponseAuthentication
yes # DԥKX{ҡIҥHA
login.conf
@@@@@@@@@@@@@@@@@@
# Ww{Ҥ觋AiAΡI
#PAMAuthenticationViaKbdInt
yes # O_ҥΨL
PAM ҲաIҥγoӼҲձN|
@@@@@@@@@@@@@@@@@@
# ɭP PasswordAuthentication ]wġI
@
# 4.3 P Kerberos
ѼƳ]wI]ڭ̨S Kerberos DAҥHUγ]wI
#KerberosAuthentication
no
#KerberosOrLocalPasswd
yes
#KerberosTicketCleanup
yes
#KerberosTgtPassing
no
@
# 4.4 UOb
X-Window UϥΪ]wI
X11Forwarding
yes
#X11DisplayOffset
10
#X11UseLocalhost
yes
# 4.5 nJ᪺ءG
PrintMotd no
# nJO_ܥX@ǸTOHҦpWnJɶBaI
@@@@@@@@@@@@@#
Aw]O yes AOApGFwAiHҼ{אּ no I
PrintLastLog
yes@@@@@# ܤWnJTIiHڡIw]]O
yes I
KeepAlive yes@@@@@@
# @ӨApG]woتܡA SSH Server |ǰe
@@@@@@@@@@@@@#
KeepAlive T Client ݡAHTO̪su`I
@@@@@@@@@@@@@#
boӱpUA@ݦA SSH iHߨ訚DIӤ|
@@@@@@@@@@@@@#
͵{Ǫo͡I
UsePrivilegeSeparation
yes # ϥΪ̪v]wءIN]w yes aI
MaxStartups
10@@@@@@# Pɤ\Xө|nJsueHڭ̳sW
SSH A
@@@@@@@@@@@@@#
O|JKXɡAoӮɭԴNOڭ̩ҿתsueաI
@@@@@@@@@@@@@#
boӳsueAFO@DAҥHݭn]w̤jȡA
@@@@@@@@@@@@@#
w]̦hQӳsueAӤwgإ߳supboQӷ
# 4.6 ϥΪ̩ת]wءG
DenyUsers *@@@@@@@
# ]wתϥΪ̦W١ApGOϥΪ̡ANO
@@@@@@@@@@@@@#
קaIYOϥΪ̡AiHNӱbJIҦpUCI
DenyUsers test
DenyGroups
test@@@@@ # P DenyUsers ۦPIȩ״XӸsզӤwI
# 5. SFTP
AȪ]wءI
Subsystem
sftp /usr/lib/ssh/sftp-server |